Blog
Cloud Security Monitoring
Many companies and organizations already rely on extensive cloud services.
However, it is not always known what is happening in the cloud, what data is in the cloud, whether an attack is taking place or data is being stolen. To monitor cloud services and minimize risks, it is therefore recommended to use a holistic monitoring system. By means of a so-called cloud security monitoring, dangers / threats and risks are monitored. If necessary, alarms can be raised quickly and efficiently, allowing an immediate response to initiate countermeasures.
Focus
The focus of cloud security monitoring lies in the holistic monitoring of the cloud infrastructure as well as a complete integration of the monitoring into the security or SOC infrastructure of an organization. For the planning of successful cloud security monitoring, it is essential to identify and clarify which technical means can be used to monitor the risks identified by the organization. This requires a detailed analysis of the existing security tools and an evaluation of these in order to assess how the identified risks can be monitored. A cloud security monitoring thrives on its data suppliers. The monitoring itself can only process and analyze the events and logs fed to it. Data suppliers and thus also the basis for monitoring are IDS & IPS, DLP systems, identity & access management, cloud assets (IaaS, Paas, Saas), security gateways,
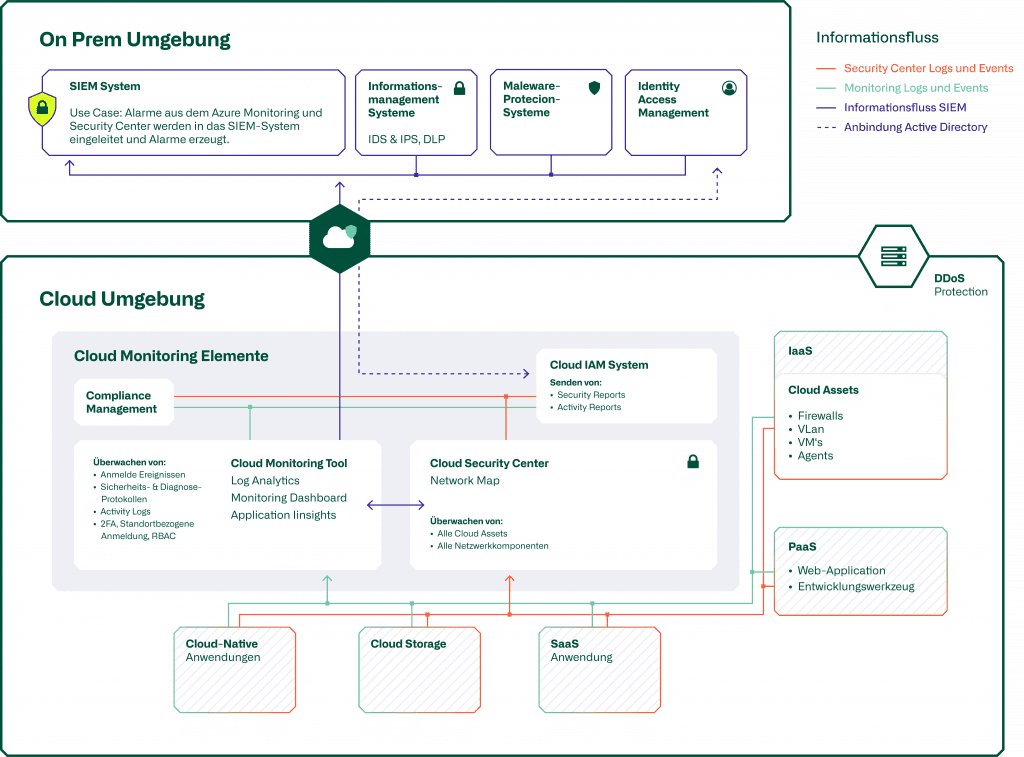
In order to avoid overhead in monitoring, the degree of monitoring must be adapted to the protection requirements of the data or the object to be protected. However, one of the most important security perimeters in the cloud is identity. It is central to being able to assign authorizations or to controlling who should have access to certain data, where and how. The use of unique identities across all infrastructure environments is therefore particularly important in order to be able to monitor activities in the cloud. Another central component is the asset management system. This is used to identify the cloud components to be monitored. Once these prerequisites have been met, successful cloud security monitoring can be set up and preferably integrated into the central SIEM system. Thus, correlations of events can be identified and the efficiency of cloud security monitoring can be increased.
A cloud security monitoring system built according to these premises has the following advantages:
- Visibility into the security state of cloud services is established.
- Compliance can be ensured by monitoring predefined pollices.
- Threats can be detected by Threat Detection, Threat Hunting and Incident Response and measures can be defined.
There are various ways in which cloud security monitoring can be set up. This strongly depends on the individual needs and the prerequisites of the respective organization.