Protect what
is important
Security for your data, applications and generally for your business - with atrete you protect what is important. As an experienced, independent and reliable partner, we are at your side for all questions regarding IT security.

Why cyber security from atrete?
Minimize IT risks, secure the basis for success
IT threats are becoming increasingly specific and complex. Your company must therefore regularly review and update its cyber security to effectively eliminate new attack vectors. We show you how.
Meeting security requirements
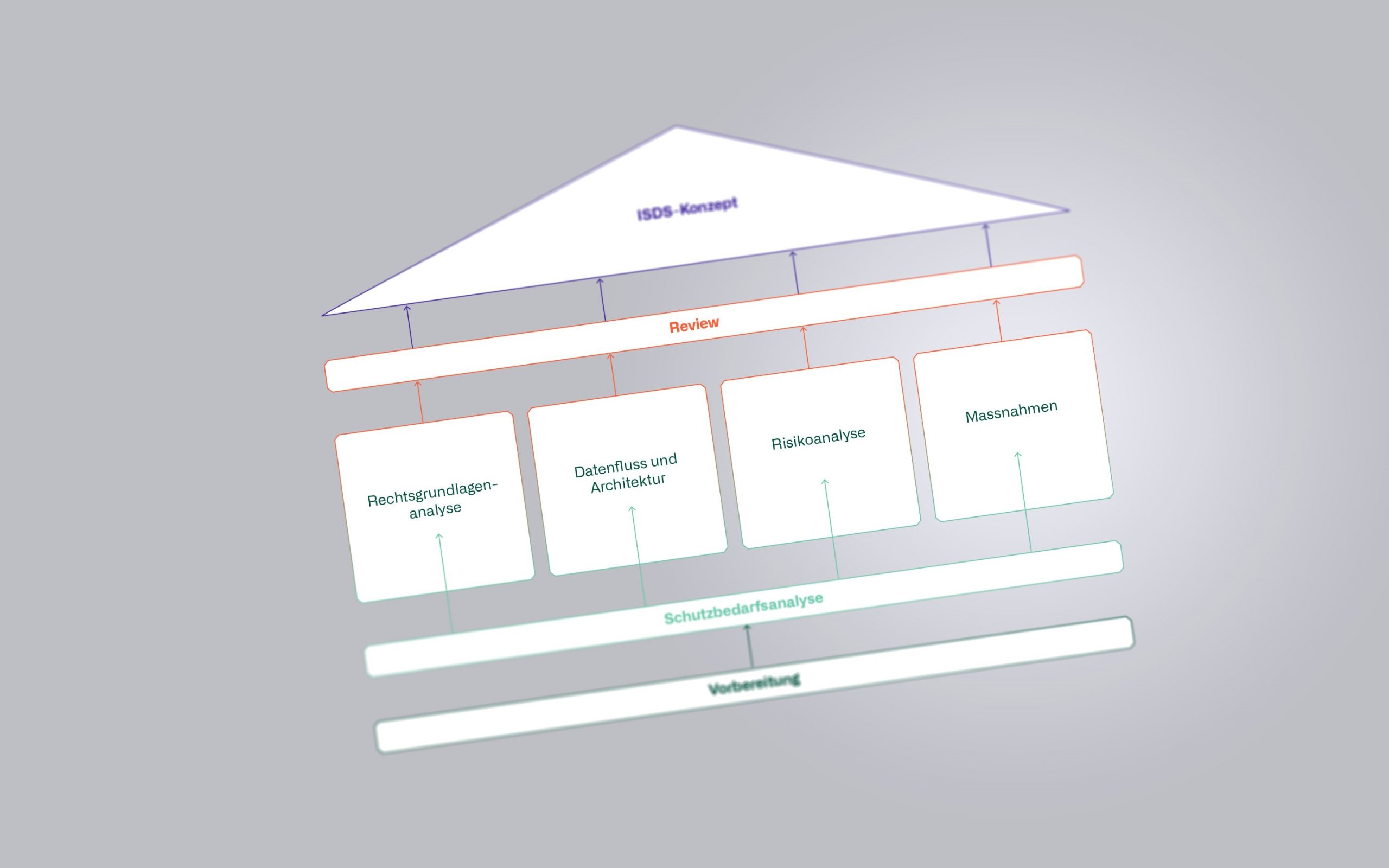
Security guidelines that are abstract and impossible to implement are ineffective. As Chief Information Security Officer (CISO), we develop a security framework that meets all requirements. We are then happy to manage your operations on the basis of the developed framework.
Achieving cyber resilience
Cyber attacks are a constant threat. They cannot be completely ruled out or prevented. But it is possible to keep the damage as low as possible. With our security concepts, you can recover your systems quickly and effectively after a cyber incident.
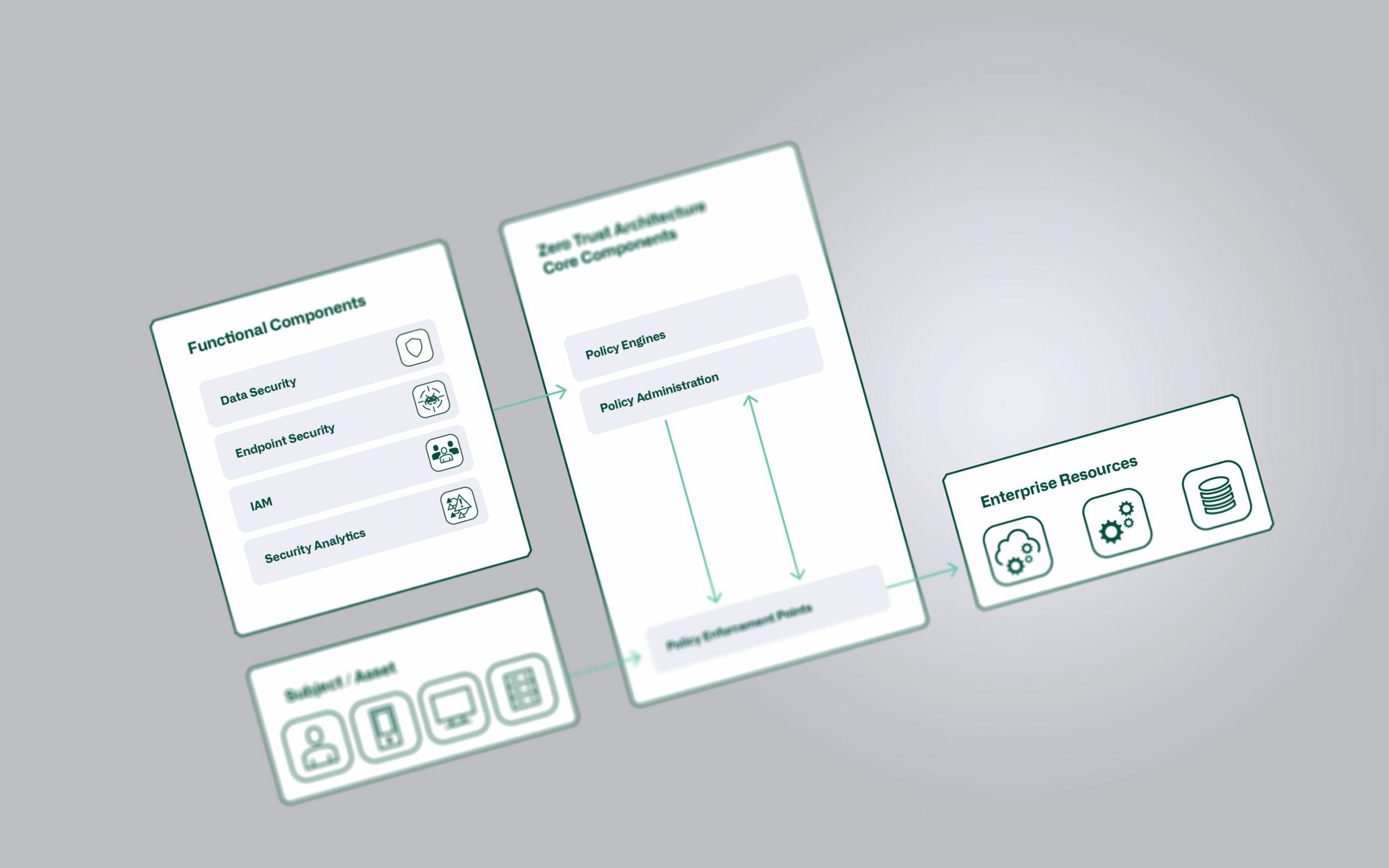
Zero Trust: more marathon than sprint
Zero Trust is still more of an idea than a product. Individual elements such as Zero Trust Network Access (ZTNA) or micro-segmentation can already be implemented. Extensive preparatory work is required for other elements. To avoid bad investments, we are developing a comprehensive strategy and roadmap.

Only neutral security advice is good security advice
As IT security experts, we advise our customers never to bet everything on one horse. The use of different providers and technologies is crucial for the protection of your systems and data. Let us talk about how we can make your IT more secure.
How atrete supports the implementation
Security concepts with vision
Consulting focus
- Are classic zone concepts still necessary?
- How do I design the optimal network segmentation?
- What do zone concepts in and with the cloud look like? Keywords: zero trust, microsegmentation.
- How do I implement a Network Access Control System?
- How do I design a secure remote access?
- How do I secure cloud access?
- How do I design the Privilege Management and its access control? Keyword: Jumphost
- What is secure Identity & Access Management?
- Is my data secure in all phases of the data life cycle?
- Do I have an adequate data security strategy?
- How secure is the data in a development environment?
- Do I need an extension of security through Data Rights Management?
- Are auditability, traceability and accountability ensured?
- How do I deal with Local Administrator privileges?
- What does my Mobile Device Management look like?
- How and where do I implement anti-virus/anti-malware systems?
- Do I have a secure and consistent approach to computer access control?
- Do I get the crucial information with an intrusion detection system?
- Is my Intrusion Prevention System configured properly?
- How do I set up Security Information and Event Management?
- Does my company need a Security Operations Center?
- Is my patch management and deployment sufficient?
- Can I optimize my IT service continuity management and IT disaster recovery setup?
- Can I meet my defined Recovery Time Objective (RTO) and Recovery Point Objective (RPO)?
- Are process adjustments necessary?
- Are there weaknesses in clustering and load balancing?
- Am I able to restore my systems after a cyber incident? What is my Mean time to recovery (MTTR)?
- Are my backups secure and is my backup management consistent?
Christoph Pfister - Head of cyber security

"Cyber incidents, malicious or not, are the biggest threat to any business in the world."
Are you interested in security consulting from atrete or the full protection of your company data?
Please contact us