Blog
Implementation of a Zero Trust Architecture
The Zero Trust Architecture has been around for years. But what are the biggest challenges and benefits today and how can such an architecture be introduced in your company?
Where are we today?
The proliferation of cloud-based services, mobile computing, Internet of Things (IoT) and Bring Your Own Device (BYOD) is changing the technology landscape for all enterprises. Existing security models are no longer sufficient to defend against new threats. Enterprises need to rethink their security architecture, and it stands to reason that the Zero Trust model will then be addressed.
As already mentioned in the introduction, the Zero Trust Architecture (ZTA) is not a new invention; this approach has existed for several years. However, there are now solutions and ways in which such an architecture can be implemented sensibly and successfully.
From various projects at our customers, from guidelines and defacto standards, we have an atrete approach on how such a Zero Trust architecture can also be introduced in your company.
Some of the biggest challenges in implementing a ZTA include:
- Leveraging existing investments and balancing priorities while moving forward.
- Deployment requires leveraging the integration of many existing technologies with varying levels of maturity
- Identify technology gaps to build the most complete ZTA possible.
- Concern that the ZTA may impact end-user operations or user experience
- Lack of a common understanding of ZTA within the organization.
However, there are also many advantages, to name a few:
- Support remote workers with access to resources regardless of their own location
- Protection of resources regardless of their location (on-prem or in the cloud)
- Limiting the insider threat (insiders are not automatically trustworthy)
- Limitation of security gaps (reduction of lateral movement and privilege escalation)
- Improve network visibility into who is accessing what resources and incident detection, including response and recovery
- Perform continuous, dynamic, and risk-based assessment of resources
What does a Zero Trust architecture entail?
Zero Trust is based, among other things, on the principle "never trust - always verify". ZTA reduces risk across the board by implementing strong identity verification, verifying device compliance, and ensuring least privilege access to only explicitly authorized resources.
Zero Trust requires that each transaction between systems (Subjects, Assets, and Resources) be validated and deemed trustworthy before the transaction can take place. The following figure shows the main components of this architecture:
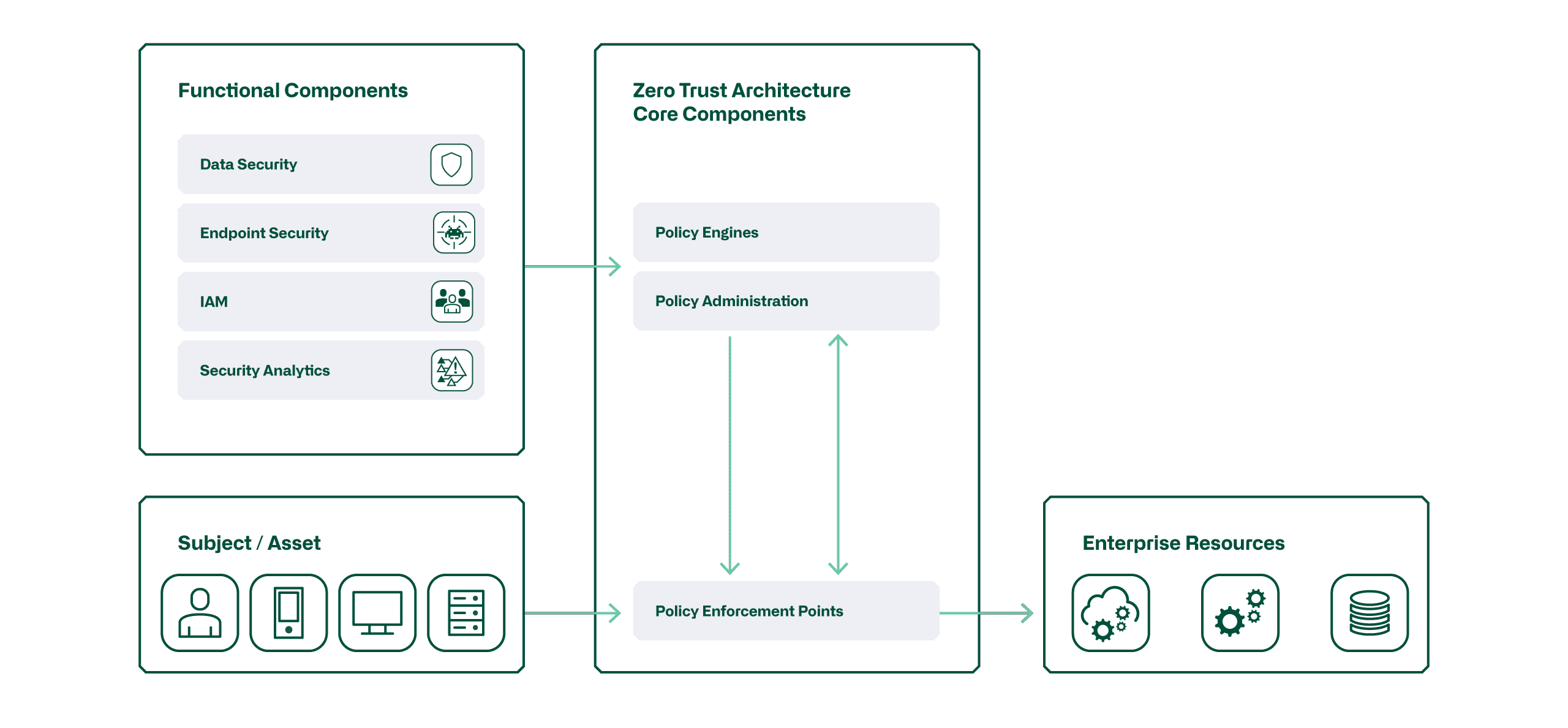
In an ideal Zero Trust environment, the following behaviors are required:
- Identities are validated and secured everywhere with multifactor authentication (MFA) to ensure that only authorized users can access protected resources.
- Devices are managed to ensure that only authorized devices can access protected networks and systems. This includes monitoring hardware and software components.
- Telemetry data is used to monitor networks and systems and detect potential threats. This includes the collection of log data, activity data and metadata.
- Access with the least privileges is enforced. Access is limited to the applications, services and infrastructure required to perform the tasks.
What is a possible course of action in each area?
The figure below shows a possible overview of the Zero Trust Maturity we aim to achieve with customers in our projects. While these maturity goals do not represent the full scope of the ZTA, they do capture the most important areas. Together with the customer, we record the current situation and determine in which areas the greatest need for action exists. The most important activities are listed per area.
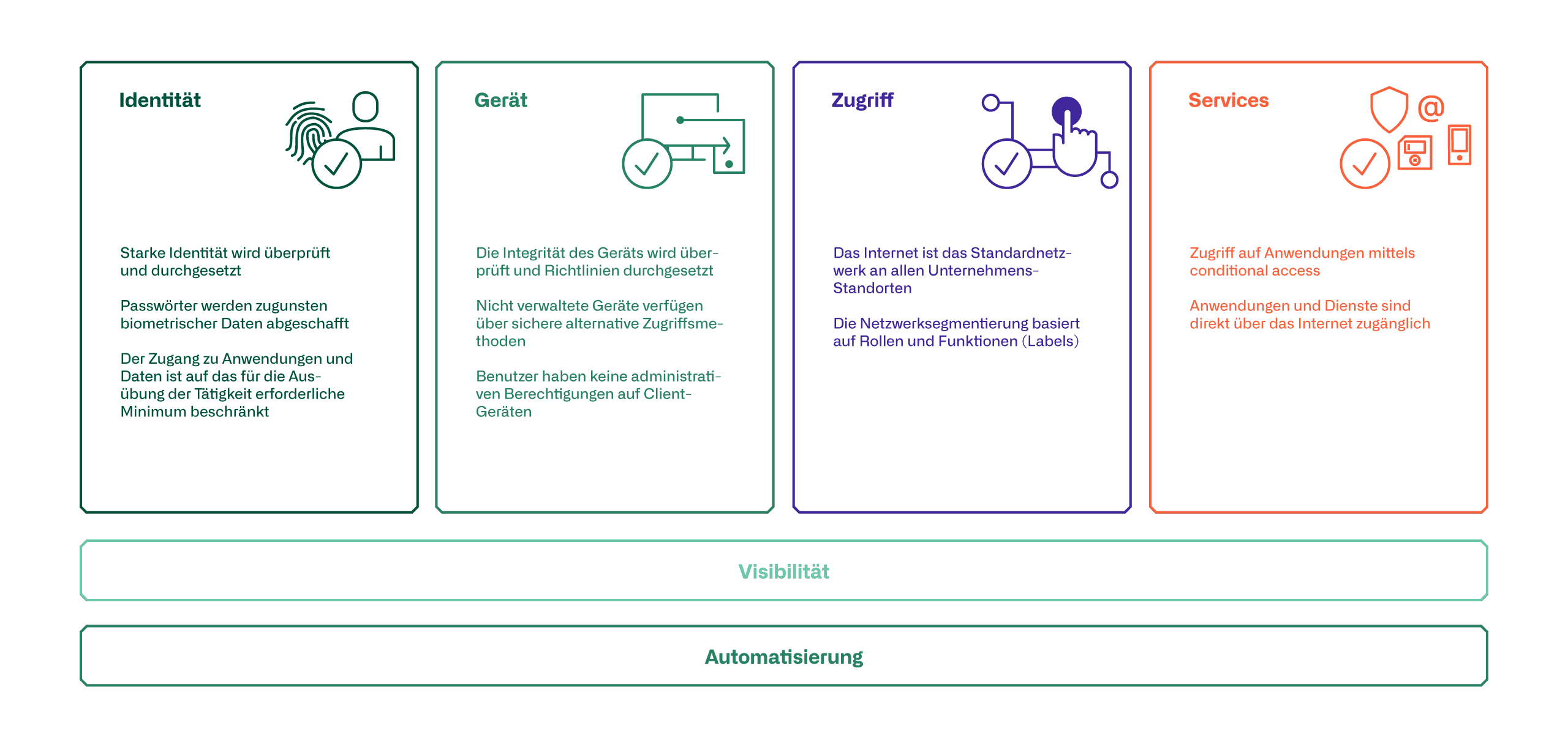
Identity
To improve identity security, it is essential that MFA be introduced to control administrative access to servers and resources. Later, this multifactor authentication requirement should be extended to all users accessing resources from outside the corporate network. A central IAM is required for this.
Device
The first step towards device verification is to register devices in a device management system. In addition, management should begin to enable proper validation of device health. This is a fundamental component to establish policies and enforce them on devices.
This applies to both company-owned devices and personal BYOD devices. If employees want to use their personal devices for access, the devices must be registered and subject to the same policies that apply to company-owned devices. For devices for which registration in device management is not possible, an alternative access option, such as a virtual desktop, is to be made available.
Access
In the area of access verification, the focus should be on segmenting users and devices (especially also IoT devices) in networks set up specifically for this purpose (macro and micro segmentation). Switching access for all employees via the Internet can be a next step toward zero trust.
Services
In order to achieve complete validation of access, older applications in particular must be modernized or special ones implemented. Replacing these legacy applications would have the additional advantage of eliminating dependence on VPN. In practice, however, this is not feasible, so hybrid solutions are needed for this.
What does the transition to a ZT architecture look like?
Each organization looking to implement a zero trust architecture must individually determine which approach and procedure best fits its environment. This includes weighing risk profiles, determining the scope of zero trust implementation, and identifying the specific checks required to access corporate resources. In all of this, fostering enterprise-wide adoption of Zero Trust is critical to success, regardless of where you choose to begin the transition.
Key findings from our projects to date:
- Collect telemetry data, assess risks, and then set goals.
- Introduce modern identities and MFA
- Focus access control enforcement on the most commonly used applications to ensure maximum coverage.
- Start with simple device health enforcement policies, such as device lockout or password complexity.
- Run pilot projects.
- Focus on the user experience because it is critical to productivity and employee morale. Without adoption, your program will not be successful.
- Communication is the key - take your employees on the journey!