Blog
Cyber disaster recovery
In this day and age, is normal disaster recovery enough to protect my organisation sufficiently against cyber-attacks?
Cyber attacks on companies in Switzerland are steadily increasing. Last year, several major Swiss companies, such as the Swatch Group, Stadler-Rail, Comparis and the Casino Theatre Winterthur, were in the headlines because they were victims of a cyber attack.
Most cyber attacks involve extortion attempts by the perpetrators. Ransomware is used to encrypt business-critical data and/or data is stolen in order to threaten publication. The latest incidents show very well that the attackers do not specifically target industries or large companies. Rather, the attackers improve their approach from time to time, so that they have the means to attack any company from a wide range of industries, whereby SMEs are not spared either. The only option left for companies to avoid being blackmailed is to restore their data. New trends in the age of digitalisation also pose a broad spectrum of challenges, as new attacks develop along with the new technologies. For example, advanced persistent threats (APTs) are increasingly common. APT is a sophisticated, long-term cyber attack in which an attacker penetrates a network undetected over an extended period of time to steal mission-critical data. Such APT attacks are carefully planned and designed to infiltrate the organisation, bypass existing security measures and remain undetected until the goal has been achieved.
Taking into account the increasingly sophisticated attacks and especially the danger that the attackers have already been in the network and systems for several months, the effectiveness of the previously known disaster recovery concepts must be questioned. Can the backup be trusted when a security incident occurs? How long has the attacker been on the systems and how far back does the backup go? In summary, the disaster recovery plan cannot be trusted in such a situation! Following the "assumption of compromise" approach, in the course of this blog we will look at one possibility of how disaster recovery should look in the future in order to counteract the danger of such APTs.
What is disaster recovery? Why does classic disaster recovery not help here?
The purpose of disaster recovery planning is to help an organisation continue to provide critical services in the event of a disruption and survive a catastrophic interruption of activities. It is about ensuring availability under information security objectives, usually being one of the last measures taken by an organisation, as all upstream, detective and protective measures have failed. Frequently encountered concepts in practice include an outsourced backup in separate locations, additional backup on tapes or possibly the outsourcing of the backup to a provider with ransomware protection. The fact is that these measures are useless against APTs, since in most cases the exact duration since the attacker's intrusion is not known. If a recovery is carried out in such a case, it must be strongly assumed that the attacker still has access to the systems and can continue his attack. But what can be done about it?
What do we mean by cyber disaster recovery? What needs to be taken into account?
While in a normal disaster recovery the backup is restored to the productive environment, the difference with cyber disaster recovery is that the restoration to the productive environment is not possible because it is assumed that it has been compromised. Depending on the goal that the company is pursuing in such a security incident, there are two possible courses of action in our view.
Action option 1 would be the classic restoration of the applications from the backup to the productive environment. If a company decides on this option, it must be strongly assumed that the restoration will have to be carried out again after a short time. Advantages of this option are the short recovery times of the applications due to low complexity as well as the avoidance of additional operating expenses for a separate system and network infrastructure. In the long term, however, this is not the best solution.
Action option 2, the long-term cyber disaster recovery solution, would provide for the recovery of applications to a separate system and network infrastructure in the event of such a security incident. Compared to action option 1, the cyber disaster recovery variant would save the effort of repeatedly restoring the systems and reduce the risk of being compromised again. On the other hand, the complexity of the recovery process of the applications and thus their recovery times increase. Likewise, the operation of a separate system and network infrastructure is likely to result in higher operating costs.
In order to find out which of the two options is right for you, we have listed the most important decision-making criteria below.
- How long may the recovery time of the applications last?
- How high can the recovery effort, i.e. the complexity, be? Do we have the necessary resources (both technical and human)?
- Effectiveness of the recovery in terms of the information security objectives of integrity and confidentiality. In other words, do you want to perform a recovery that allows re-infection or not?
- Functionality of the applications - Means whether the system can be used in isolation or only in a network with other interfaces?
Which option is chosen in the end is up to the joint decision of business and IT.
In order for a cyber disaster recovery to be set up in the company, the following preparatory tasks must be carried out:
- Establishment of a separate / isolated system and network infrastructure
- Develop cyber recovery plans for the various applications and their systems
We will take a closer look at both preparation tasks within this blog post in order to sharpen our understanding of cyber disaster recovery in these two tasks.

cyber security
We are at your side for all questions regarding IT security
Read more here
Cyber Recovery Infrastructure
In order to be able to solve the scenario described above, it is essential that a separate system and network infrastructure is operated for cyber disaster recovery. It is important that the necessary infrastructure for the clients is also considered. This should also be kept in place for a disaster.
When designing the cyber recovery infrastructure, it is important to define the scope in advance. This information can be used to determine how large the environment needs to be or, in other words, how much computing power and storage needs to be kept in the separated environment. In principle, we recommend keeping this environment as small as possible in order to keep the operating costs as low as possible. Ideally, the scope should focus on the essential, business-critical applications and their systems of your company.
The next important aspect in connection with the cyber recovery infrastructure concerns the isolation of this environment. This raises two questions that you need to answer for yourself:
- How independent does the cyber recovery infrastructure need to be from the productive environment?
- Does one share systems from the productive environment for the operation of the cyber recovery infrastructure or does it need its own systems?
Both of the points mentioned above have a major influence on the operating costs. After all, it must be taken into account that the operation (patching, lifecycle, etc.) for the cyber recovery infrastructure must be guaranteed in the same way as for the productive environment.
What must not be forgotten is the third aspect of the cyber recovery infrastructure. The segregated environment must have an Active Directory service. Without it, operation is not possible.
When implementing a cyber recovery infrastructure, it makes sense to consider a cloud provider. By setting up the environment in the cloud, the administrative effort of the management systems for the cyber recovery infrastructure can be reduced to a minimum. Many operational tasks that arise with an on-premises solution are eliminated with a cloud solution.
Cyber Recovery Plans
The second preparatory task is the development of cyber recovery plans. At this point, disaster recovery plans should be defined for each application group. The aim of the plans should be to serve the IT department in the form of a step-by-step guide to action in the event of a disaster. However, it is crucial that, compared to the usual recovery plans, the cyber recovery plans do not only rely on the recovery process of the systems from the backup. In such a case, it is necessary for the Cyber Recovery Plan of an application network to show how the backup can be composed from various sources. We have illustrated the principle below.
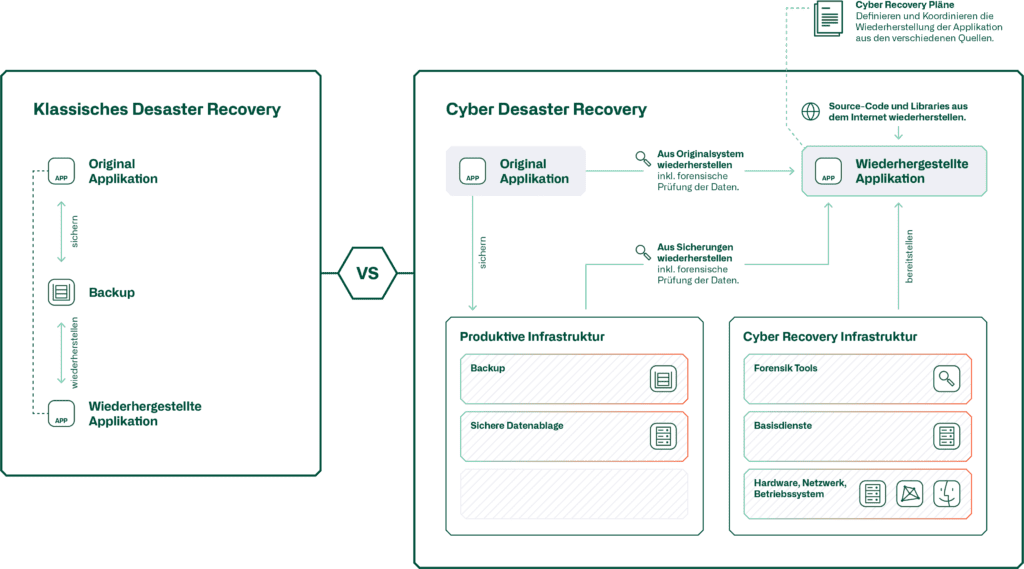
Another key point that must be included in the cyber recovery plans is the listing of the dependencies that applications have on other systems. It is essential to clearly define these dependencies in order to know which applications need to be restored or present in order to guarantee the full functionality of the business-critical applications.
How we can support you
Revising the disaster recovery concept requires much more than just setting up a second separate infrastructure at a second location. In addition, Business Continuity Plan (BCP) aspects must also be questioned and revised according to the new cyber recovery plans. These are, among others, points such as:
- Clear definition of responsibilities in the plan
- Clearly identify the persons responsible for each function in the plan
- Step-by-step description of the recovery process
- Clear identification of the various resources required for the recovery and continued operation of the organisation
- Determine and communicate the circumstances within the organisation under which the disaster recovery plan should be declared.
It is important to emphasise that, depending on the complexity of the organisation, one or more plans can be created for the different aspects of BCP and disaster recovery. These plans do not necessarily need to be integrated into a single plan. However, each plan must be consistent with the other plans in order to end up with a viable BCP strategy.
As can be seen, as with any technological change, some technical, administrative as well as operational hurdles have to be overcome when adapting the disaster recovery plan - we are happy to support you in this.