CISO-as-a-Service
Chief Information Security Officer of atrete
With CISO-as-a-Service, atrete offers companies a security officer who can cover requirements and needs around the topic of information security.
CISO-as-a-Service stands for flexibility: The atrete Chief Information Security Officer can be deployed ad interim, full-time or part-time, for topic-specific support or also in projects.
Tailored to the task, atrete contributes the know-how and experience of its employees in the areas of security governance, risk management, security audits and best practice in the implementation of security technologies.
Our Chief Information Security Officer Service Package
We have structured the CISO-as-a-Service package roughly according to ISO 27001 - of course, each subject area can also be dealt with individually or in combination with other areas so that customer requirements can be optimally covered.
- Security Management: Assessment of the existing Information Security Management
- Development of a security strategy with the description of the legal requirements, alignment with frameworks such as ISO27001, organisation and processes of information security
- Establish security management on the basis of a security strategy:
- IT Risk Management
- Data inventory and data classification
- Specification documents for projects: Protection needs analysis, security concept and data protection impact assessment
- Formulation of the security policy in the form of guidelines for users (policies) but also IT (defined operating processes, specifications and technical standards as well as procedures)
- Development and implementation of a company-wide security policy with the corresponding directives or policies (e.g. secure handling of the IT infrastructure).
- Design and implementation of business continuity management: emergency management and disaster recovery planning as well as regular exercises
- Establishment and maintenance of an ISMS
- Definition and implementation of measures for staff sensitisation, user awarenesstrainings
- Support in the planning and implementation of security measures in projects: Risk analysis, development of safety measures and assessment of residual risks
- Realisation of authentication & access management
- Coordination with projects relevant to information and data security
- Security monitoring and reporting
- Regular control of information security by means of process and technology audits
Our approach
The successful development and implementation of a comprehensive information security management system (ISMS) takes place top-down. This ensures that the company's goals or strategy are taken into account and that the implementation is supported by the company's management.
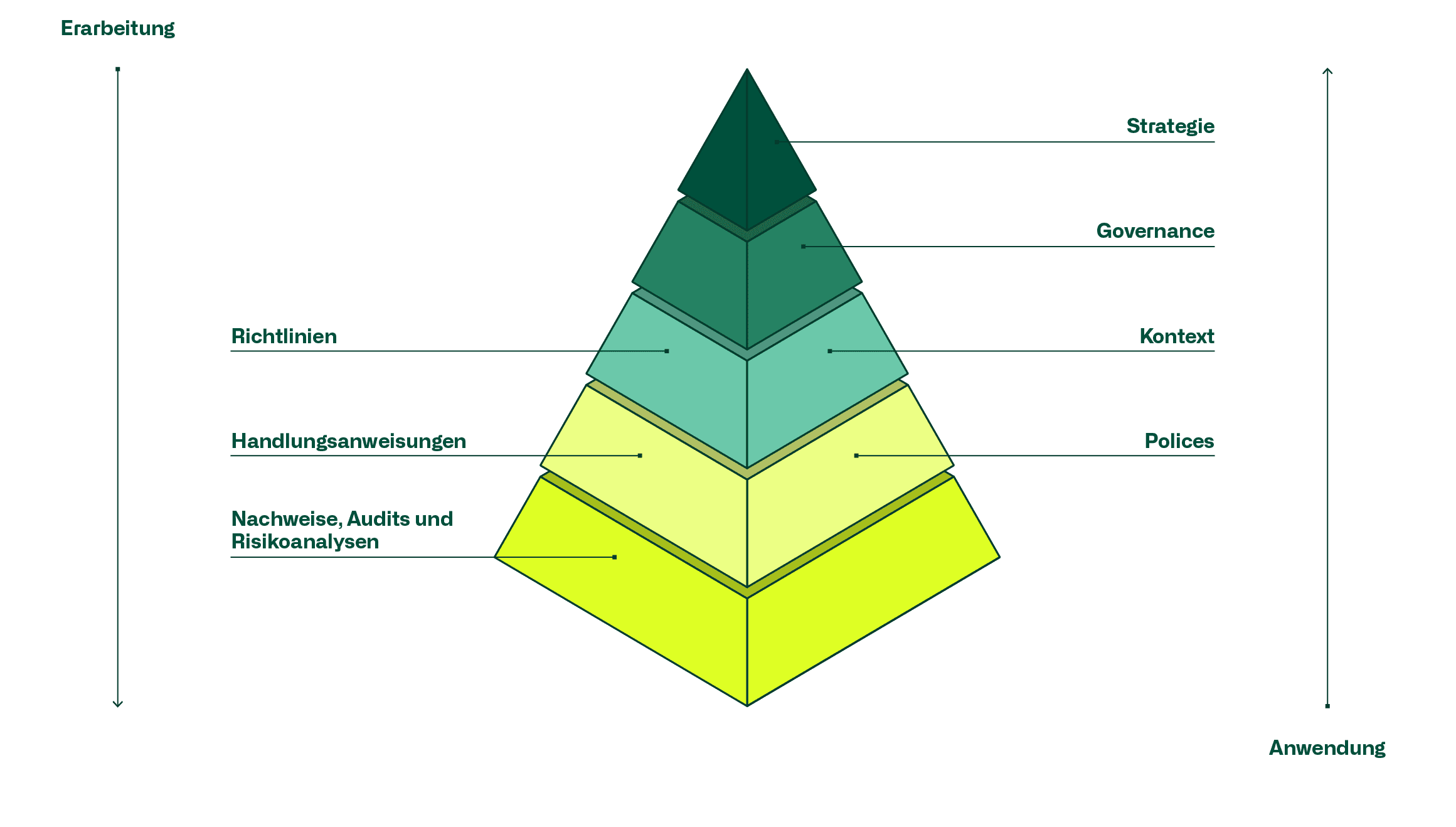
The application of the Information Security Management System (ISMS), on the other hand, is driven bottom-up and is based on evidence, checks (audits) and risk analyses, which are checked against the specifications (guidelines, action instructions and technical policies) and assessed in the context of the company and the applicable regulatory requirements.
Our experienced and certified consultants have distinctive expertise to carry out the development, implementation and application of security-relevant tasks for you and thus act as representatives between the company management and the IT departments and their users. Our consultants work exclusively in the cyber security environment and therefore always have the latest information and certifications.