Information security and data protection (ISDS) concept made easy
In the digital age, where data and information is the new gold, information security and privacy (ISDS) has become a critical concern for businesses worldwide.
The 18th century proverb "a good preparation is half the battle" has proven itself over time for a wide variety of challenges. This also applies to the creation of an ISDS concept. Thanks to our many years of experience, we can now pass on practical tips and tricks for creating an ISDS concept. Whether you are a small startup or an established company, the importance of a solid ISDS concept cannot be overstated.
The pillars of an ISDS concept
A good ISDS concept is based on a solid foundation consisting of the preparation and protection needs analysis as well as the four pillars illustrated below.
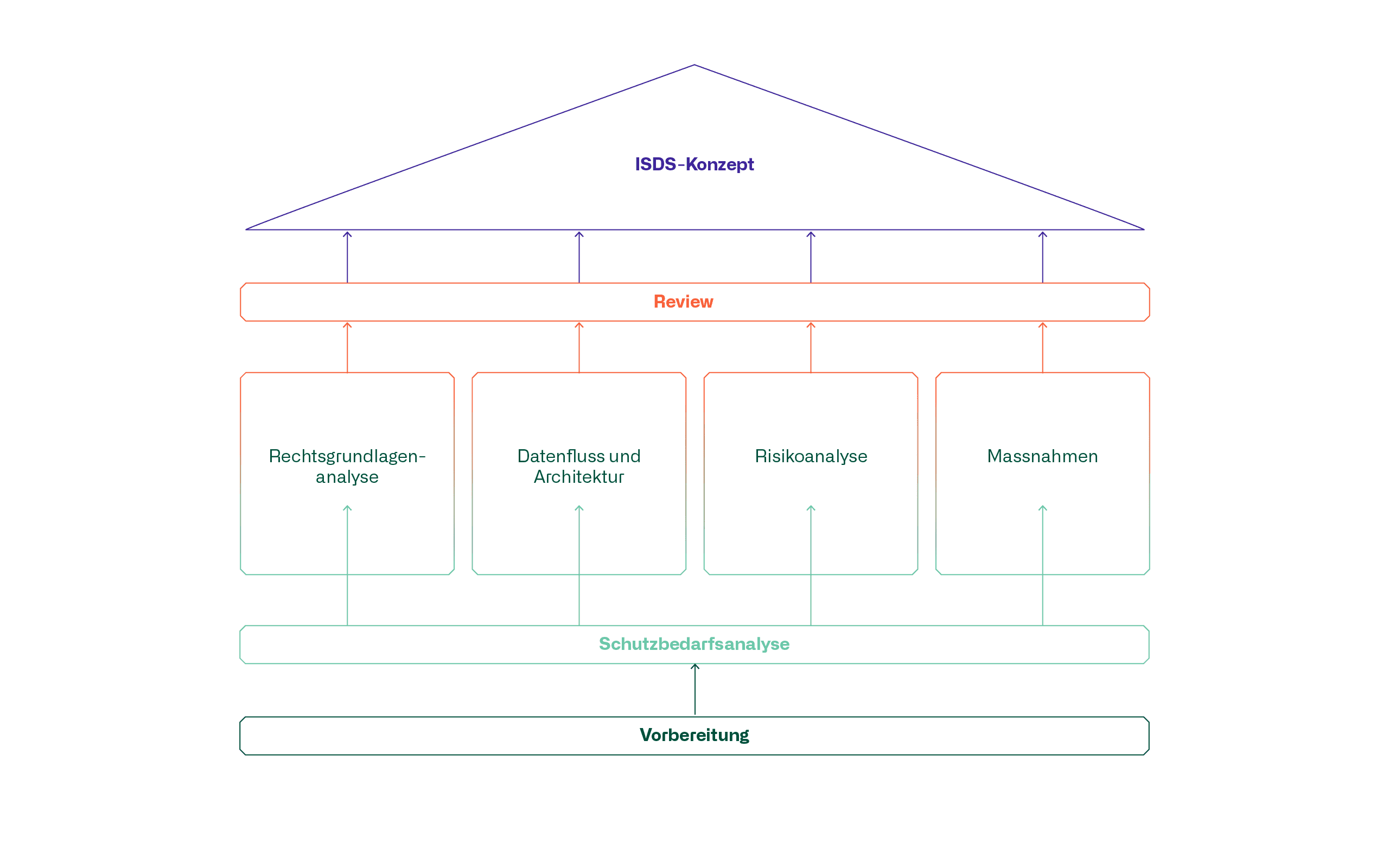
Preparation
Preparation is the cornerstone of any successful ISDS concept. Before you dive deep into the matter, it is crucial to identify all the roles involved.
The roles required for the creation of an ISDS concept are as follows:
- Project manager
- IT architect
- Information Security Officer
- Data protection consultant
- Data owner and/or risk owner
- Risk manager
- Legal department
The project manager is responsible for developing the ISDS concept.
The IT architect knows the connections, the scope and the schema of the applications and is therefore predestined to provide the required information on the data flows.
The Information Security Officer (ISO) is responsible for checking and evaluating the plausibility, effectiveness and conformity with the security architecture of the risk analysis and the proposed measures for dealing with the risks.
The Data Protection Advisor (DPO) supports the controller or processor in all matters relating to the protection of personal data.
The data owner is responsible for the data and information within their assigned area (specific application, service, etc.). He creates the protection requirements analysis as part of the ISDS concept.
The risk owner decides on the residual risks, taking into account the company's risk appetite. He therefore accepts the proposed measures to reduce the risks and bears the residual risks of the undertaking upon acceptance.
The risk manager is informed about the risks relevant to the company following the ISDS concept. He ensures that all formalities (approval process, documentation, etc.) have been complied with.
The legal department has the expertise to prepare a correct legal basis analysis. This analysis is very individual. Depending on whether a company is public or private and whether it operates in specific sectors, very different legal or regulatory requirements may apply that affect the project and its risks and measures.
Protection needs analysis
The protection requirements analysis is the starting point in the process of developing an ISDS concept. It aims to identify the critical values and assess their protection requirements based on a selected classification, e.g. Federal Office for Information Security (BSI IT-Grundschutz), International Organization for Standardization (ISO 27001), etc. Basically, the aim is to assess the protection goals of confidentiality, availability, integrity and traceability and assign them a protection level: e.g. normal, high or very high protection requirements. If it turns out after the protection needs analysis that there is no increased need for protection, you are already at the end here and do not need to create an ISDS concept, provided that the company's basic IT protection measures are complied with.
The protection requirements analysis can be created efficiently if a template is used that automatically identifies the appropriate protection requirements for each protection objective using company-specific questions and drop-down answers.
Analysis of the legal basis
The legal basis analysis deals with external requirements (laws and regulations) and internal requirements (governance).
The central questions that need to be answered by the legal basis analysis relate to the risks resulting from violations of compliance or governance requirements:
- What: Is there anything that prevents me from implementing my planned project?
- How: Is there anything that prevents me from implementing my planned project?
The key point is that the company knows and is aware of the requirements that must be met. In most cases, these requirements relate specifically to the Data Protection Act in the area of implementation.
If the current business case does not differ significantly from previous projects or the core business area, the legal basis analysis can be adopted depending on the risk appetite. If necessary, a legal opinion from industry associations can also be used; such principles have broad support.
Data flow and architecture
A data flow diagram depicts how data flows through a system, including the sources, destinations, storage and processes that handle the data. This visualization helps to develop a clear understanding of how information moves through the organization, which is critical for identifying potential security risks and dependencies.
The focus of the data flow analysis is on the interfaces between systems.
A risk analysis is used to check whether the use of an interface is associated with an additional risk, e.g. a transition from DMZ to intranet, data center to cloud, or even data flows between countries.
To ensure that the risk survey is complete, particular attention should be paid to the interfaces. The completeness of the description can be supported by means of checklists.
Risk analysis
The prerequisite for a risk analysis is that the risk management framework and risk acceptance are clearly defined. The protection levels of the protection objectives derived from the protection requirements analysis are checked by means of a risk analysis if they exceed the normal protection requirements.
As a first step, it makes sense to compile a set of mandatory measures into a basic protection catalog. This enables the checklist approach to evaluate the implementation of the measures. Basic protection measures that have not been implemented represent a potential risk that must be addressed by means of the risk analysis. Protection goals whose level of protection exceeds the normal level of protection must be analyzed in more detail in the next step.
The following diagram describes the risk analysis process using a fictitious protection requirements analysis:
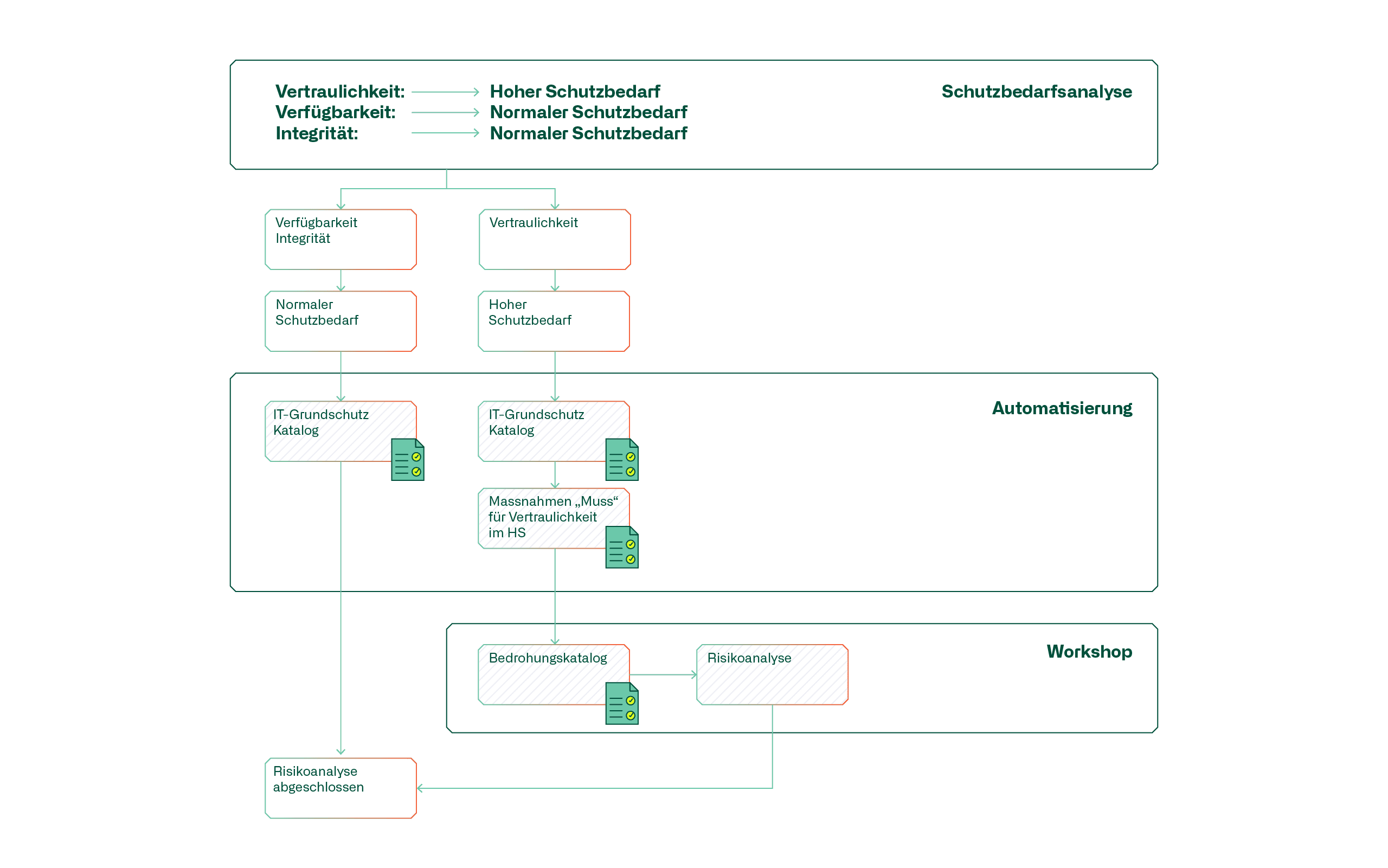
This procedure can be automated using appropriate tools, thus creating sufficient scope for the actual risk analysis.
Experience has shown that it is advisable to organize the risk analysis in the form of a workshop consisting of the project manager, the architect and the information security officer in order to examine the project from the perspective of a bad actor. A bad actor would ask themselves, for example: In what way can I misuse a system? Where can data be stolen? How large is the attack surface of an insider threat, how are attacks detected and prevented? These questions are compiled into a catalog of threats.
To ensure that the project plan is examined from A to Z, the risks from the identified threats are discussed and evaluated in relation to the systems and interfaces of the data flow diagram. The process is repeated, taking into account the risk mitigation measures, in order to identify the residual risk.
Measures
Monitoring and controlling measures ensures that they are implemented in operations. Automation is also an option here, so that those responsible for implementation are reminded and reporting is made possible.
Review
The procedure described here is suitable for all companies. In order to best adapt the procedure to the individual company, we recommend the introduction of a review process, similar to a continuous improvement process. This process should ensure that the knowledge gained during the creation of the ISDS concepts is integrated into the process. One focus is on increasing the degree of automation of the first step of the risk analysis, whereby the defined measures from the previous review period are examined as a supplement to the mandatory measures. In addition, the focus is on the further development of the threat catalog as a basis for future risk analyses.
Secure the future of your company with us: We help you to develop your individualized ISDS process. Our many years of consulting experience will help us to help you. Creating ISDS concepts should not be a laborious undertaking. There is a smarter way: with atrete.
New head of cyber security
Christoph Pfister joined our team as Head of cyber security on March 1, 2024. We are delighted to welcome such an experienced IT specialist to our team. With over 25 years of experience in IT, media and financial services, our new colleague brings a proven track record in building, developing and leading high-performance teams. In recent years, he has worked as CIO and Senior Technology Strategy Consultant of financial market regulated SaaS and IT service providers, leading complex cloud migration and go-to-market projects and programs.
His expertise includes business-IT alignment, technology and cloud strategies, enterprise architecture, product management and development, go-to-market strategies, IT governance, information security and compliance in a regulated environment.
Christoph Pfister holds a Bachelor of Science in Business Information Technology, a Master of Science in Business Administration and an Executive Master of European and International Business Law from the University of St. Gallen. He is currently deepening his knowledge with a Master's degree in Financial Markets Compliance at the HWZ University of Applied Sciences in Business Administration Zurich.
We are convinced that his extensive knowledge and innovative approach will help us to achieve our goals and write new success stories.

Media contact:
at rete ag
Marlene Haberer
Phone: +41 44 266 55 83
Email: marlene.haberer@atrete.ch
atrete further expands consultant team
In recent months, the renowned consulting firm atrete has added three new talented members to its team to strengthen its CIO Advisory, Digital Workplace and Cybersecurity divisions.



Jessica Knecht has been supporting the team in the CIO Advisory practice area as an Associate Consultant since April 1, 2023.
Ms. Knecht brings extensive experience in the IT sector, particularly in IT Service Management and Cloud Provider Management. Prior to joining atrete, she worked for several years as a Customer Service Manager at a renowned IT service provider. She holds a degree in Technical Business Administration and has completed a CAS in IT Sourcing and Provider Management at ZHAW. She is also certified in IT Service Management (ITIL Foundation), Requirements Engineering (IREB Foundation) and Microsoft Azure Fundamentals.
Vivien Bührer joined the Digital Workplace and Collaboration practice as a Consultant on June 1, 2023.
Ms. Bührer has an impressive career that includes time as a Solution Designer for End User Services at Fujitsu. In this role, she managed tenders for managed workplace services and advised on IT service management topics. She holds a Master of Science in Business Analytics, Controlling and Consulting and also brings qualifications such as Scrum Master, Hermes and ITIL certifications.
atrete warmly welcomes Sven Gerig, who has been supporting the Cybersecurity Practice Area as a Consultant since June 12, 2023.
Mr. Gerig can look back on a successful career with various IT service providers in the Zug region, where he worked as a project manager and systems engineer. His extensive knowledge is also reflected in his certifications, including Azure Solutions Architect Expert, Cybersecurity Architect Expert and Enterprise Administrator Expert in Microsoft. He also brings qualifications such as SAFe® Scrum Master and ITIL 4 Foundation. Soon he will complete his degree as dipl. Informatiker HF Fokus Cyber Security.
Media contact:
at rete ag
Marlene Haberer
Phone: +41 44 266 55 83
Email: marlene.haberer@atrete.ch
Implementation of a Zero Trust Architecture
Where are we today?
The proliferation of cloud-based services, mobile computing, Internet of Things (IoT) and Bring Your Own Device (BYOD) is changing the technology landscape for all enterprises. Existing security models are no longer sufficient to defend against new threats. Enterprises need to rethink their security architecture, and it stands to reason that the Zero Trust model will then be addressed.
As already mentioned in the introduction, the Zero Trust Architecture (ZTA) is not a new invention; this approach has existed for several years. However, there are now solutions and ways in which such an architecture can be implemented sensibly and successfully.
From various projects at our customers, from guidelines and defacto standards, we have an atrete approach on how such a Zero Trust architecture can also be introduced in your company.
Some of the biggest challenges in implementing a ZTA include:
- Leveraging existing investments and balancing priorities while moving forward.
- Deployment requires leveraging the integration of many existing technologies with varying levels of maturity
- Identify technology gaps to build the most complete ZTA possible.
- Concern that the ZTA may impact end-user operations or user experience
- Lack of a common understanding of ZTA within the organization.
However, there are also many advantages, to name a few:
- Support remote workers with access to resources regardless of their own location
- Protection of resources regardless of their location (on-prem or in the cloud)
- Limiting the insider threat (insiders are not automatically trustworthy)
- Limitation of security gaps (reduction of lateral movement and privilege escalation)
- Improve network visibility into who is accessing what resources and incident detection, including response and recovery
- Perform continuous, dynamic, and risk-based assessment of resources
What does a Zero Trust architecture entail?
Zero Trust is based, among other things, on the principle "never trust - always verify". ZTA reduces risk across the board by implementing strong identity verification, verifying device compliance, and ensuring least privilege access to only explicitly authorized resources.
Zero Trust requires that each transaction between systems (Subjects, Assets, and Resources) be validated and deemed trustworthy before the transaction can take place. The following figure shows the main components of this architecture:
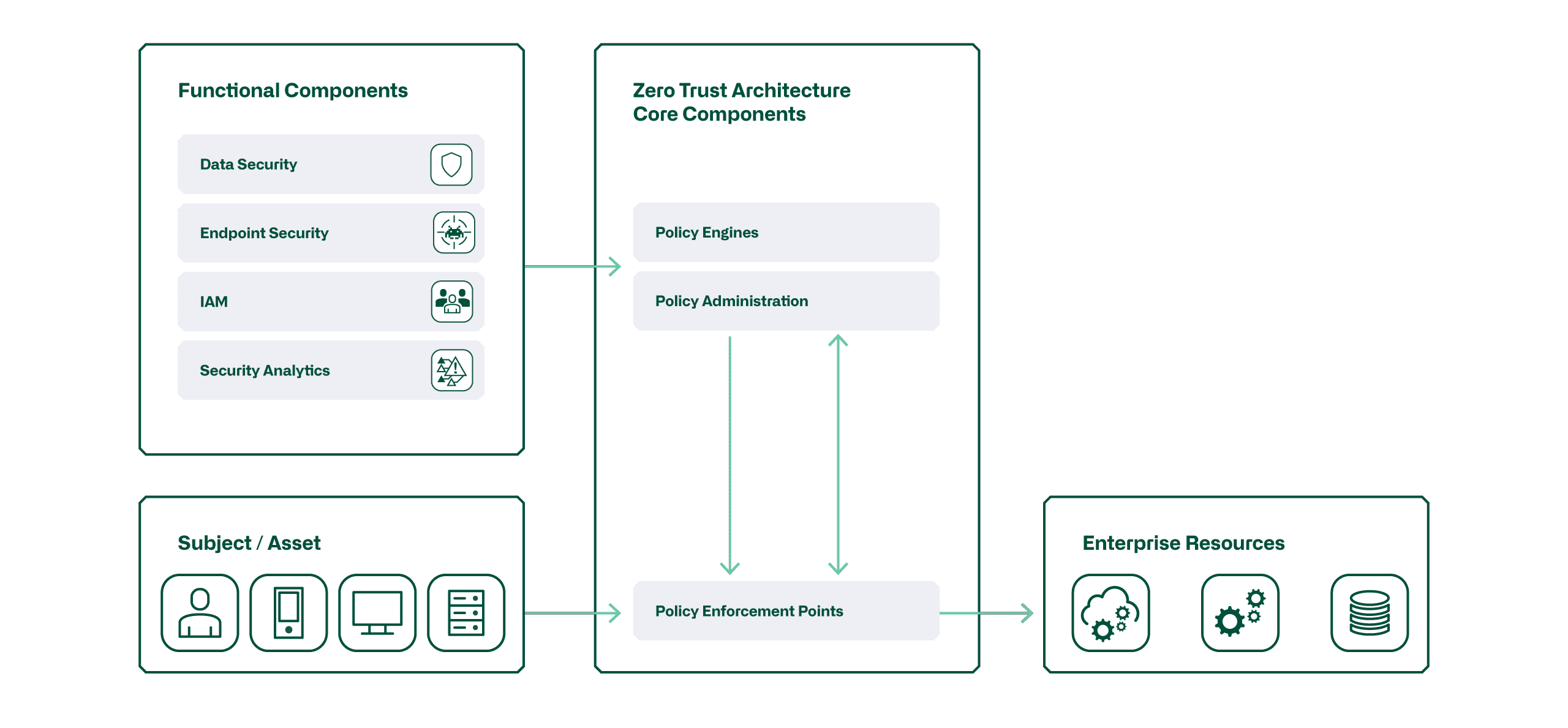
In an ideal Zero Trust environment, the following behaviors are required:
- Identities are validated and secured everywhere with multifactor authentication (MFA) to ensure that only authorized users can access protected resources.
- Devices are managed to ensure that only authorized devices can access protected networks and systems. This includes monitoring hardware and software components.
- Telemetry data is used to monitor networks and systems and detect potential threats. This includes the collection of log data, activity data and metadata.
- Access with the least privileges is enforced. Access is limited to the applications, services and infrastructure required to perform the tasks.
What is a possible course of action in each area?
The figure below shows a possible overview of the Zero Trust Maturity we aim to achieve with customers in our projects. While these maturity goals do not represent the full scope of the ZTA, they do capture the most important areas. Together with the customer, we record the current situation and determine in which areas the greatest need for action exists. The most important activities are listed per area.
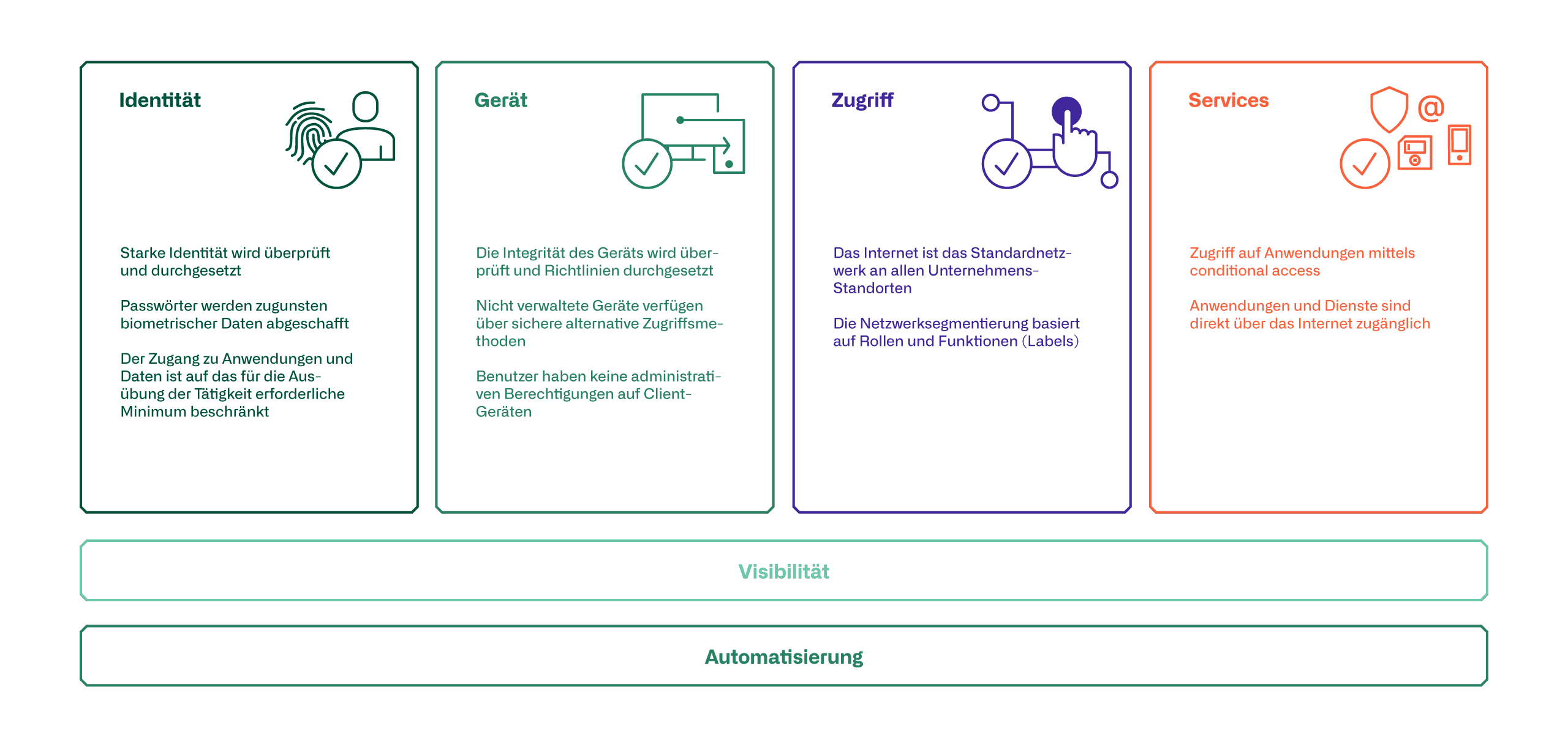
Identity
To improve identity security, it is essential that MFA be introduced to control administrative access to servers and resources. Later, this multifactor authentication requirement should be extended to all users accessing resources from outside the corporate network. A central IAM is required for this.
Device
The first step towards device verification is to register devices in a device management system. In addition, management should begin to enable proper validation of device health. This is a fundamental component to establish policies and enforce them on devices.
This applies to both company-owned devices and personal BYOD devices. If employees want to use their personal devices for access, the devices must be registered and subject to the same policies that apply to company-owned devices. For devices for which registration in device management is not possible, an alternative access option, such as a virtual desktop, is to be made available.
Access
In the area of access verification, the focus should be on segmenting users and devices (especially also IoT devices) in networks set up specifically for this purpose (macro and micro segmentation). Switching access for all employees via the Internet can be a next step toward zero trust.
Services
In order to achieve complete validation of access, older applications in particular must be modernized or special ones implemented. Replacing these legacy applications would have the additional advantage of eliminating dependence on VPN. In practice, however, this is not feasible, so hybrid solutions are needed for this.
What does the transition to a ZT architecture look like?
Each organization looking to implement a zero trust architecture must individually determine which approach and procedure best fits its environment. This includes weighing risk profiles, determining the scope of zero trust implementation, and identifying the specific checks required to access corporate resources. In all of this, fostering enterprise-wide adoption of Zero Trust is critical to success, regardless of where you choose to begin the transition.
Key findings from our projects to date:
- Collect telemetry data, assess risks, and then set goals.
- Introduce modern identities and MFA
- Focus access control enforcement on the most commonly used applications to ensure maximum coverage.
- Start with simple device health enforcement policies, such as device lockout or password complexity.
- Run pilot projects.
- Focus on the user experience because it is critical to productivity and employee morale. Without adoption, your program will not be successful.
- Communication is the key - take your employees on the journey!
We are happy to support you in the analysis, design and implementation of a Zero Trust architecture.
Cyber disaster recovery
Cyber attacks on companies in Switzerland are steadily increasing. Last year, several major Swiss companies, such as the Swatch Group, Stadler-Rail, Comparis and the Casino Theatre Winterthur, were in the headlines because they were victims of a cyber attack.
Most cyber attacks involve extortion attempts by the perpetrators. Ransomware is used to encrypt business-critical data and/or data is stolen in order to threaten publication. The latest incidents show very well that the attackers do not specifically target industries or large companies. Rather, the attackers improve their approach from time to time, so that they have the means to attack any company from a wide range of industries, whereby SMEs are not spared either. The only option left for companies to avoid being blackmailed is to restore their data. New trends in the age of digitalisation also pose a broad spectrum of challenges, as new attacks develop along with the new technologies. For example, advanced persistent threats (APTs) are increasingly common. APT is a sophisticated, long-term cyber attack in which an attacker penetrates a network undetected over an extended period of time to steal mission-critical data. Such APT attacks are carefully planned and designed to infiltrate the organisation, bypass existing security measures and remain undetected until the goal has been achieved.
Taking into account the increasingly sophisticated attacks and especially the danger that the attackers have already been in the network and systems for several months, the effectiveness of the previously known disaster recovery concepts must be questioned. Can the backup be trusted when a security incident occurs? How long has the attacker been on the systems and how far back does the backup go? In summary, the disaster recovery plan cannot be trusted in such a situation! Following the "assumption of compromise" approach, in the course of this blog we will look at one possibility of how disaster recovery should look in the future in order to counteract the danger of such APTs.
What is disaster recovery? Why does classic disaster recovery not help here?
The purpose of disaster recovery planning is to help an organisation continue to provide critical services in the event of a disruption and survive a catastrophic interruption of activities. It is about ensuring availability under information security objectives, usually being one of the last measures taken by an organisation, as all upstream, detective and protective measures have failed. Frequently encountered concepts in practice include an outsourced backup in separate locations, additional backup on tapes or possibly the outsourcing of the backup to a provider with ransomware protection. The fact is that these measures are useless against APTs, since in most cases the exact duration since the attacker's intrusion is not known. If a recovery is carried out in such a case, it must be strongly assumed that the attacker still has access to the systems and can continue his attack. But what can be done about it?
What do we mean by cyber disaster recovery? What needs to be taken into account?
While in a normal disaster recovery the backup is restored to the productive environment, the difference with cyber disaster recovery is that the restoration to the productive environment is not possible because it is assumed that it has been compromised. Depending on the goal that the company is pursuing in such a security incident, there are two possible courses of action in our view.
Action option 1 would be the classic restoration of the applications from the backup to the productive environment. If a company decides on this option, it must be strongly assumed that the restoration will have to be carried out again after a short time. Advantages of this option are the short recovery times of the applications due to low complexity as well as the avoidance of additional operating expenses for a separate system and network infrastructure. In the long term, however, this is not the best solution.
Action option 2, the long-term cyber disaster recovery solution, would provide for the recovery of applications to a separate system and network infrastructure in the event of such a security incident. Compared to action option 1, the cyber disaster recovery variant would save the effort of repeatedly restoring the systems and reduce the risk of being compromised again. On the other hand, the complexity of the recovery process of the applications and thus their recovery times increase. Likewise, the operation of a separate system and network infrastructure is likely to result in higher operating costs.
In order to find out which of the two options is right for you, we have listed the most important decision-making criteria below.
- How long may the recovery time of the applications last?
- How high can the recovery effort, i.e. the complexity, be? Do we have the necessary resources (both technical and human)?
- Effectiveness of the recovery in terms of the information security objectives of integrity and confidentiality. In other words, do you want to perform a recovery that allows re-infection or not?
- Functionality of the applications - Means whether the system can be used in isolation or only in a network with other interfaces?
Which option is chosen in the end is up to the joint decision of business and IT.
In order for a cyber disaster recovery to be set up in the company, the following preparatory tasks must be carried out:
- Establishment of a separate / isolated system and network infrastructure
- Develop cyber recovery plans for the various applications and their systems
We will take a closer look at both preparation tasks within this blog post in order to sharpen our understanding of cyber disaster recovery in these two tasks.

cyber security
We are at your side for all questions regarding IT security
Read more here
Cyber Recovery Infrastructure
In order to be able to solve the scenario described above, it is essential that a separate system and network infrastructure is operated for cyber disaster recovery. It is important that the necessary infrastructure for the clients is also considered. This should also be kept in place for a disaster.
When designing the cyber recovery infrastructure, it is important to define the scope in advance. This information can be used to determine how large the environment needs to be or, in other words, how much computing power and storage needs to be kept in the separated environment. In principle, we recommend keeping this environment as small as possible in order to keep the operating costs as low as possible. Ideally, the scope should focus on the essential, business-critical applications and their systems of your company.
The next important aspect in connection with the cyber recovery infrastructure concerns the isolation of this environment. This raises two questions that you need to answer for yourself:
- How independent does the cyber recovery infrastructure need to be from the productive environment?
- Does one share systems from the productive environment for the operation of the cyber recovery infrastructure or does it need its own systems?
Both of the points mentioned above have a major influence on the operating costs. After all, it must be taken into account that the operation (patching, lifecycle, etc.) for the cyber recovery infrastructure must be guaranteed in the same way as for the productive environment.
What must not be forgotten is the third aspect of the cyber recovery infrastructure. The segregated environment must have an Active Directory service. Without it, operation is not possible.
When implementing a cyber recovery infrastructure, it makes sense to consider a cloud provider. By setting up the environment in the cloud, the administrative effort of the management systems for the cyber recovery infrastructure can be reduced to a minimum. Many operational tasks that arise with an on-premises solution are eliminated with a cloud solution.
Cyber Recovery Plans
The second preparatory task is the development of cyber recovery plans. At this point, disaster recovery plans should be defined for each application group. The aim of the plans should be to serve the IT department in the form of a step-by-step guide to action in the event of a disaster. However, it is crucial that, compared to the usual recovery plans, the cyber recovery plans do not only rely on the recovery process of the systems from the backup. In such a case, it is necessary for the Cyber Recovery Plan of an application network to show how the backup can be composed from various sources. We have illustrated the principle below.
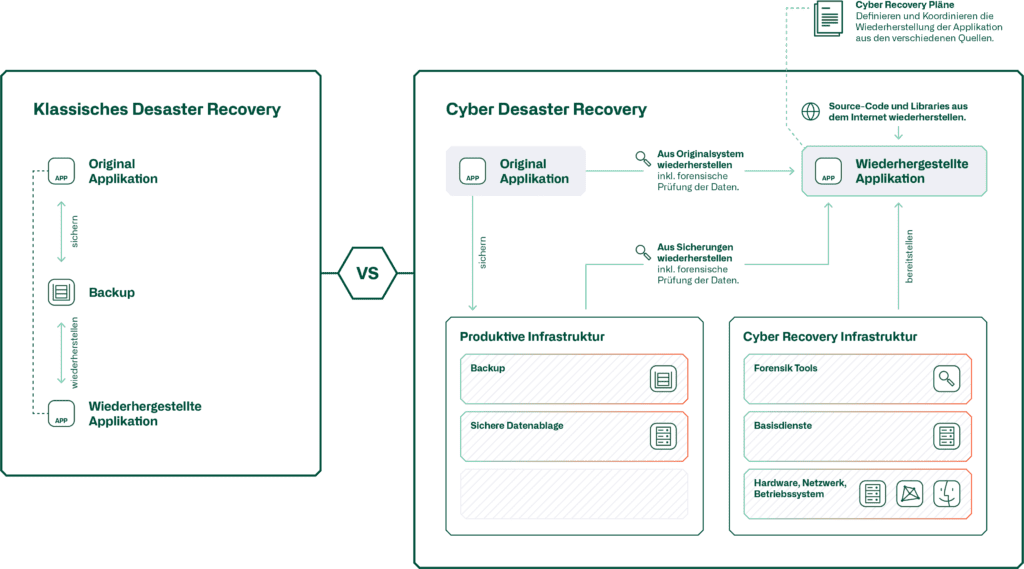
Another key point that must be included in the cyber recovery plans is the listing of the dependencies that applications have on other systems. It is essential to clearly define these dependencies in order to know which applications need to be restored or present in order to guarantee the full functionality of the business-critical applications.
How we can support you
Revising the disaster recovery concept requires much more than just setting up a second separate infrastructure at a second location. In addition, Business Continuity Plan (BCP) aspects must also be questioned and revised according to the new cyber recovery plans. These are, among others, points such as:
- Clear definition of responsibilities in the plan
- Clearly identify the persons responsible for each function in the plan
- Step-by-step description of the recovery process
- Clear identification of the various resources required for the recovery and continued operation of the organisation
- Determine and communicate the circumstances within the organisation under which the disaster recovery plan should be declared.
It is important to emphasise that, depending on the complexity of the organisation, one or more plans can be created for the different aspects of BCP and disaster recovery. These plans do not necessarily need to be integrated into a single plan. However, each plan must be consistent with the other plans in order to end up with a viable BCP strategy.
As can be seen, as with any technological change, some technical, administrative as well as operational hurdles have to be overcome when adapting the disaster recovery plan - we are happy to support you in this.
With our broad know-how and experience from various projects at different companies, we can help your company overcome the challenges and improve security thanks to the benefits. We are able to pick up and engage the right people so that their disaster recovery plan can withstand the latest cyber threats. Only with the right roles, the right processes, the appropriate commitment and a well thought-out concept can the additional security measures also be operated within a sensible framework.
atrete strengthens the Cyber Security and Digital Workplace & Collaboration teams
The IT consulting company atrete strengthens its consulting team with the two consultants Sven Köppel and Aldo Richner.


Sven Köppel has been working as a consultant in the Digital Workplace area since 1.9.2021. Prior to atrete, he worked for an IT service provider in the Zug region for several years, most recently in a key role in the introduction of IT infrastructure projects with a focus on digital workplace topics. In addition to a degree from a higher technical college as a certified technician HF in information technology, he also holds Microsoft certifications, including Microsoft 365 Certified Enterprise Administrator Expert.
Aldo Richner joined the Cyber Security Team as a consultant on 1 October 2021. He has several years of experience as a system engineer. His initial focus was on the operation and further development of the IT infrastructure as well as the implementation of complex changes to sourcing infrastructures. In recent years, he has increasingly taken on tasks in the area of cybersecurity. Aldo Richner holds a BSc in Business Informatics from the University of Applied Sciences FHNW as well as certifications in Requirements Engineering (IREB Foundation), ITIL Foundation in IT Service Management. He is currently in training for the "CAS Cybersecurity and Information Risk Management" at the FHNW.
Microsegmentation: advantages and challenges
Microsegmentation protects individual workloads, provides more transparency and also makes compliance easier and more effective. In addition to the technological challenges, there are also some organizational challenges that need to be considered and overcome during implementation.
As recent cyber incidents (including Solarwinds) have shown, cyber criminals with their vast resources are able to compromise all types of businesses in any industry and regardless of whether it is on-prem or cloud infrastructure. Micro-segmentation is often cited as a solution to the problem: Improved visibility of network connections, protection against APTs (Advanced Persistent Threats), interdiction of lateral movement, and end-to-end compliance.
What is microsegmentation?
If you are completely new to this term, or concept, I would like to briefly discuss in this paragraph what micro-segmentation means and how an organization can implement it to protect their confidential and sensitive digital assets.
In a few words: Microsegmentation makes it possible to subdivide the network very finely granular and independent of classic network segments and IP addresses, typically down to individual workloads. For each (micro)segment, security controls (whitelist approach) must then be defined based on data security requirements.
Traditionally, perimeter and zone firewalls have been the primary defense mechanism to prevent unauthorized access to systems or applications. However, outdated rules, misconfigurations, open ports, reused IP addresses, etc. can allow malicious actors to penetrate your organization's network infrastructure. This leads to compromise of critical applications, operating systems or servers and threatens the security of data. Microsegmentation increases the granularity of filtering, creating virtual or host-based firewalls for each endpoint on the network. The gained visibility and ability to define connections in a very granular way supports the formulation of strict and specific security policies and helps to minimize the points of attack and make it difficult to spread in the network.
Advantages of microsegmentation
There are several benefits of micro-segmentation, the most important of which are listed below:
- Protects individual workloads: Microsegmentation security reduces attack surfaces and protects individual applications and workloads that may also be distributed across different infrastructures, such as in a multi-cloud environment. The very granular restriction of connections can prevent lateral movement.
- Increased automation: Automation with a strong focus on integration via interfaces (resulting in new possibilities for dynamic rule creation), centralization, and reusable security policy templates (predefined and approved connections) provide significant time savings and prevent overuse of expensive resources.
- Simplified compliance: Micro-segmentation simplifies compliance with regulations such as PCI-DSS, HIPAA or GDPR by clearly defining the scope of application and the ability to push segmentation across all environments such as hybrid and multi-cloud. This creates the opportunity to implement cross-platform auditable and automated processes that can be quickly adapted to new compliance requirements as needed.
- Cross-infrastructure segmentation: Microsegmentation provides a simple, modern and secure solution for environment segregation, no matter where and on which infrastructure your systems run. For example, productive data on the on-prem infrastructure and systems from the development environment in the public cloud can be segregated in a very granular way.
- Improved visibility: Microsegmentation tools, which often evolved from analytics tools, provide centralized, granular, real-time visibility across all connections in the network, reducing the time required to assess and remediate issues in hybrid environments. The visibility gained also allows attacks to be detected more quickly and thus APTs to be better defended against.
Implementation challenges
Implementing microsegmentation also comes with challenges:
- Adaptation of the infrastructure: The implementation will require changes to the network topology and architecture. In order to minimize the financial effort and the risk of failures, a defined procedure based on the analysis of the traffic relationships is necessary.
- Adaptation of processes: Whether it is the process for new systems or the process for requesting new connections, a holistic view and optimization of the processes is required. The processes must be optimized and automated to such an extent that the additional measures can also be implemented operationally. The partially newly required or newly assigned roles must be supported by the management. For example, all communication relationships must be defined and recorded by the application manager, which sometimes means a paradigm shift in the mindset of the employees - automation and the use of appropriate tools can help here.
- Integration into the existing tool landscape: Automation and the use of appropriate tools should help to implement the additional security measures as simply as possible and support employees in their new tasks. Microsegmentation only works with good orchestration and integration into existing tools via open interfaces.
- Policy Lifcyle: Due to the considerable increase in information security guidelines and security policies, a corresponding lifecycle management is required. Here, too, the corresponding tools can help and support, but they must be integrated into any existing systems.
- Know how about the applications: It is necessary that the application managers know and understand their application and especially its network connections. It is not enough that the systems are provided once and then the corresponding rules are created based on the analyzed connections. Basically, there is no connection if it has not been defined before. Support is provided with appropriate tools and analyses, but the mindset of the employees also plays a role here.
How we can support you
Adapting the strategy of traditional zoning to micro-segmentation requires not only technical adjustments and the introduction of new tools to manage hybrid environments (including existing classic firewalls for perimeter or client protection). Rather, it is an adjustment of mindset, an adjustment of the processes of how systems and applications are deployed, how connections are requested, a shift of responsibilities, and a path into automation of the network infrastructure. It's about incorporating the entire lifecycle of an application, from development to release to tear down. It's about orchestrating different infrastructures (on-prem, hybrid or multi-cloud) and implementing policies across technologies (host-based, network-based, cloud native).
However, as with any technological change, implementing micro-segmentation requires overcoming a number of technical, administrative, and operational hurdles - and we can help.
With our broad know-how and experience from various projects at different companies, we can help your company overcome the challenges and improve security thanks to the benefits. We are able to pick up and involve the right employees accordingly, so that the change to micro-segmentation is a success. Only with the right roles, the right processes, the appropriate commitment and a well thought-out concept can the additional security measures also be operationally operated within a meaningful framework.